posted on March 12, 2023, 5:51 a.m.
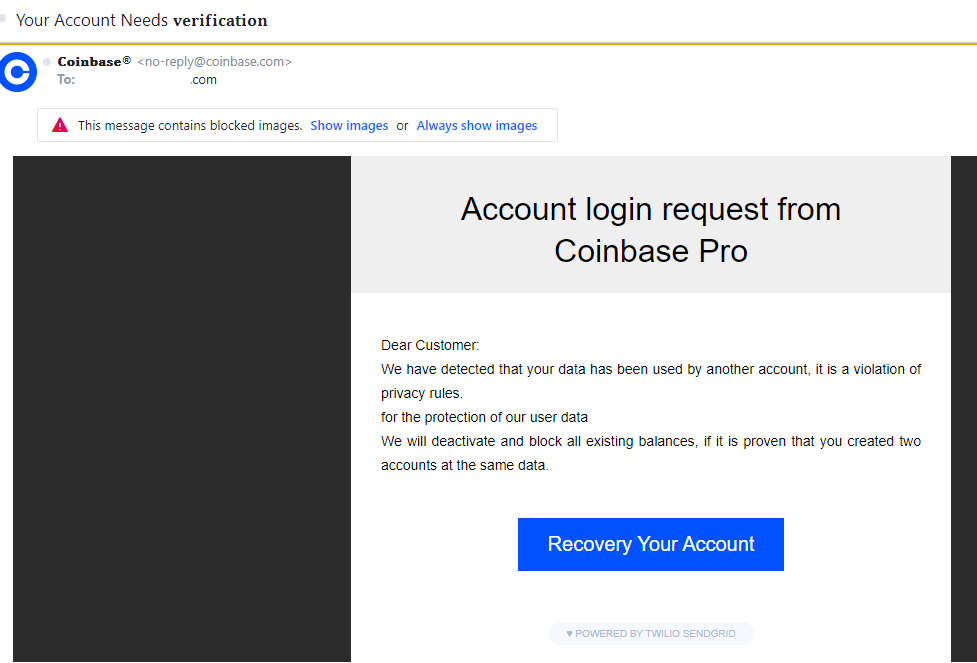
This is the email:
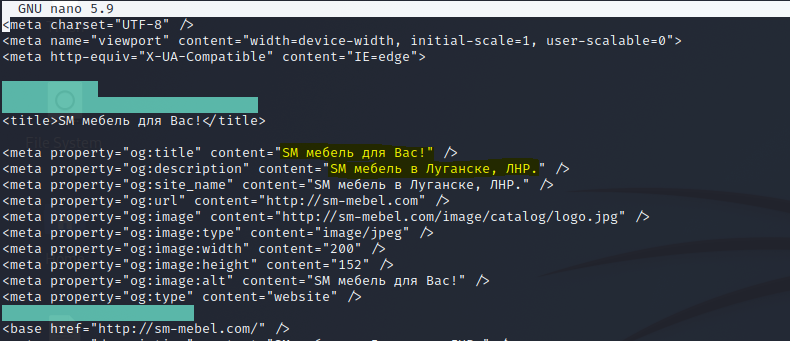
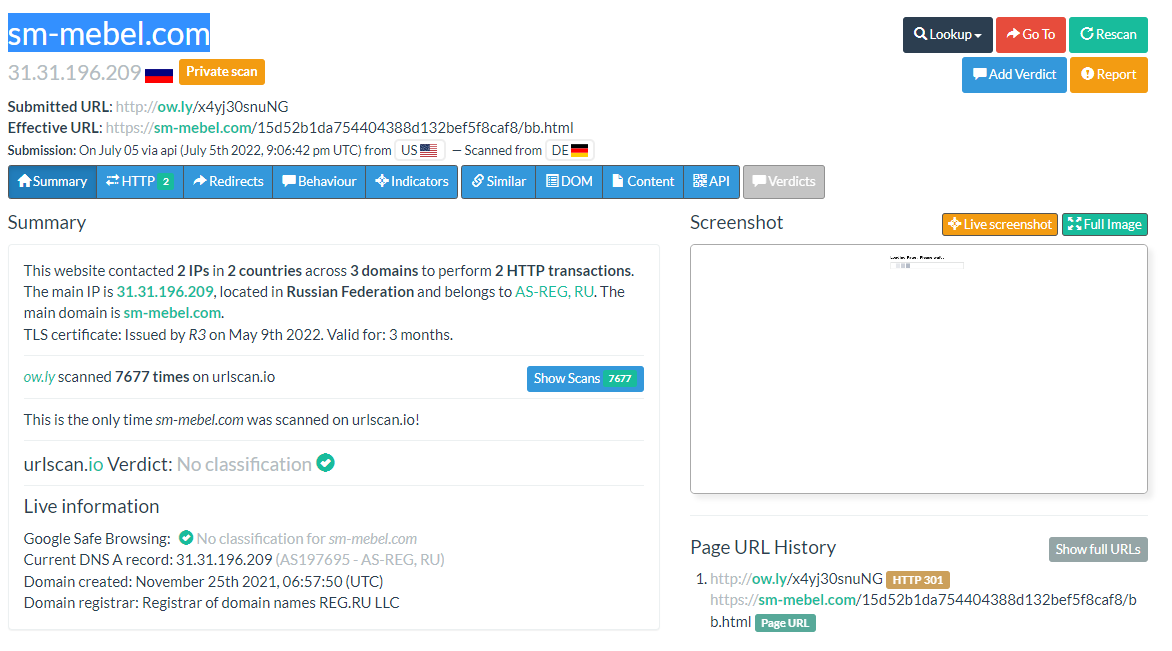
the link is an ow[.]ly redirect to sm-mebel[.]com which then redirects you to the final domain: accesspoint-cnt-ce22.cjonline[.]org
If we grab the full url:
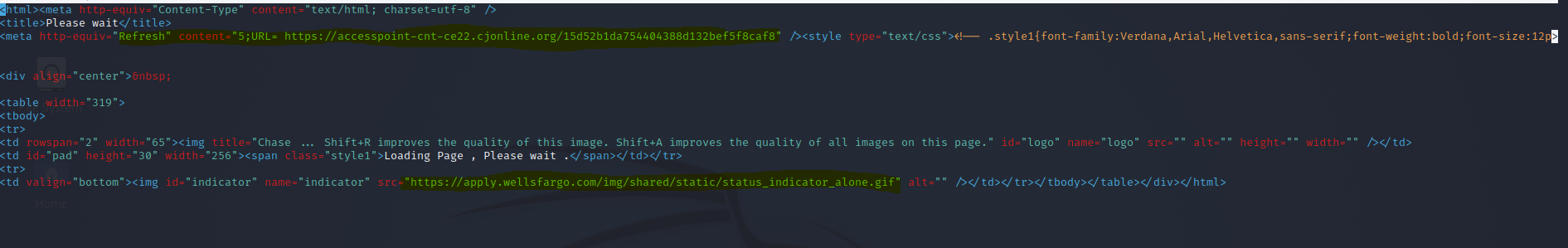
and inspect it, we find that this landing page, after clicking the link on the email, shows a a wellsfargo(cheeky) loading animation and then redirects you to the final malicious page using <meta http-equiv="refresh" content="..." to send you there.
This is what it looked like:
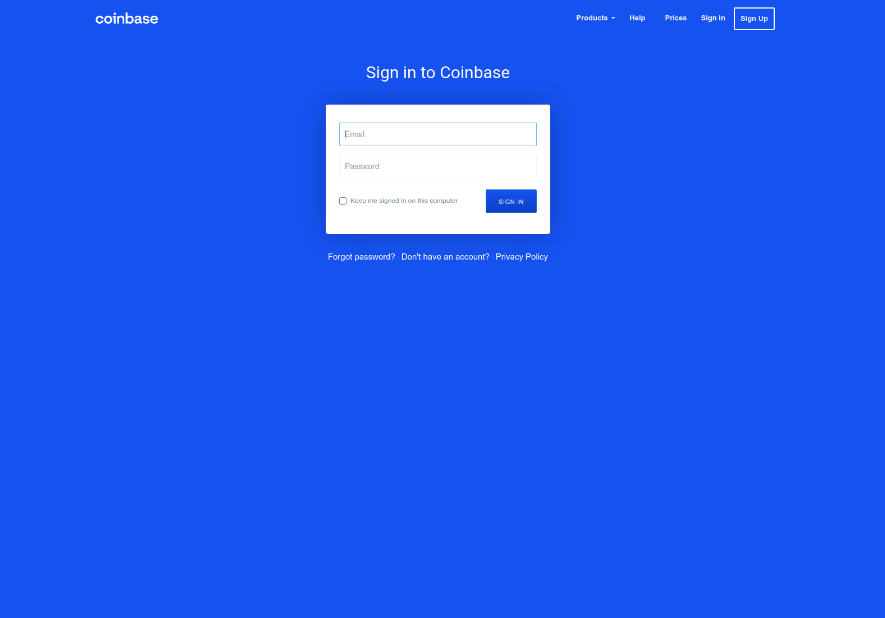
And here is where you finally land:
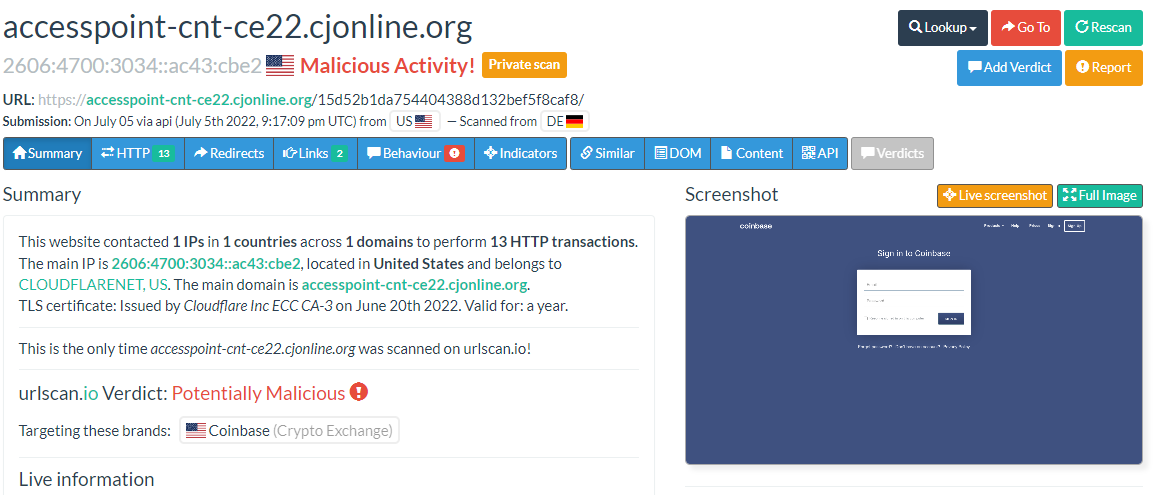
Here is the urlscan results of the page:
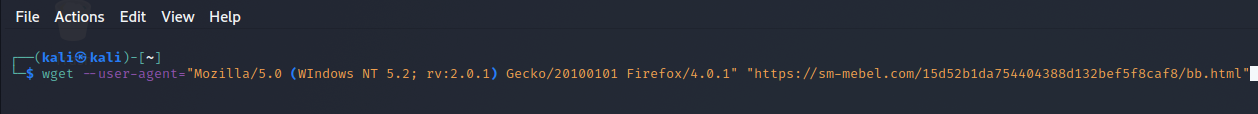
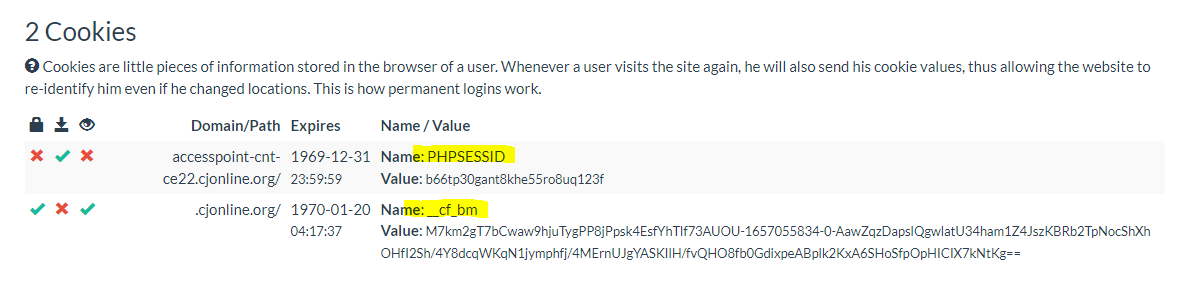
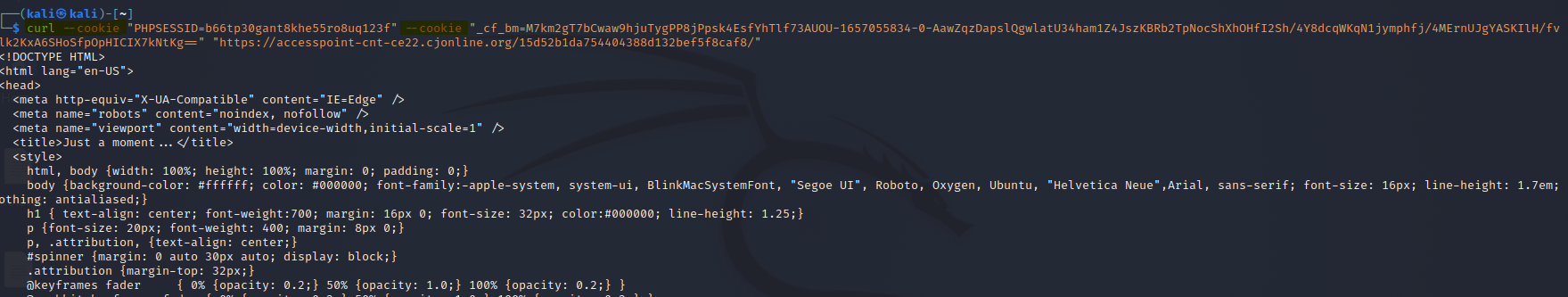
Now, in order to successfully request the html code of the page in bash, I had to set two cookies, "phpsessid" and "_cf_bm" with the curl command options. I used the cookies created in the urlscan detonation:
The command:
Without the two headers, the request would result in a 403 forbidden.
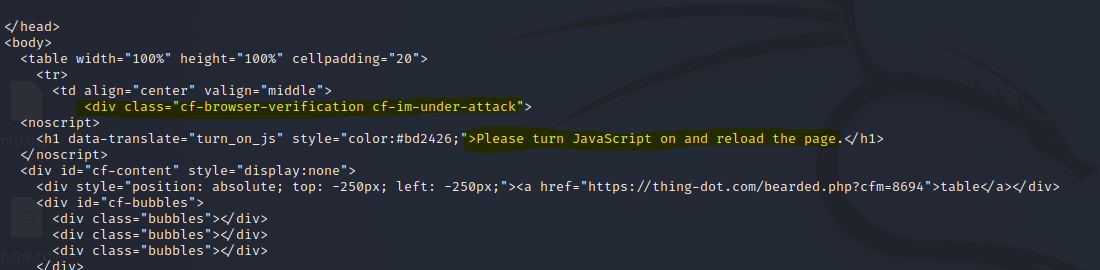
And finally I hit a road block with bash-only-based investigation, the dreaded javascript:
I cannot go any further unless i use more sophisticated techniques.